Mobile Phishing is on the Rise
Cyber criminals are cashing in on the fact that phishing is today’s number one mobile threat affecting companies. In fact, Wandera’s 2018 Phishing Report shows that “Mobile users are 3 times more likely to fall prey to phishing on mobile, than they are on desktops,” says Michael Covington,vice president at Wandera. Not only that, mobile users are 18 times more likely to be exposed to phishing attempts.
Why is Mobile Phishing the easier target?
There’s simply less suspicion of links and attachments on mobile devices. With corporate mobile devices containing SMS, Skype, WhatsApp, social media, email, and games, criminals are taking advantage reaching employees with more personal interactions.
“As more communications take place over mobile devices, organizations haven’t changed their thinking to cover the modes of communications taking place on the devices,” according to Covington.

Do you use a Corporate Device?
Mobile devices are an extension of your company’s network and holds a wealth of sensitive valuable data. The price for your breached credentials on the dark web are increasing in price, suggesting they’re higher in demand. In fact, it’s not just the contacts, cached emails, photos, documents, and other sensitive data, it’s also the direct access to you company’s VPN that can lead to compromising your company’s internal network.
Mobile Users Are the First to Arrive
Most fraudulent phishing emails call for immediate action. Most victims of phishing scams that fall for this will quickly click on the link to the phishing website. The first users to visit the link are the most vulnerable. This is because many phishing attacks are blocked by phishing filters or taken down within the first couple of hours.
Remember:
- Mobile users are “always on” and are most likely to read email messages as soon as they arrive
- Desktop users only read messages when they have access to their computers
Mobile phishing is growing
- The average iOS mobile user is 18x more likely to encounter a phishing attack than a malware attack
- A new mobile phishing page is launched every 20 seconds. That’s more than 4,000 new phishing sites per day
- 5% of all successful mobile phishing attacks take place on dating apps
- 90% of cyberattacks start with a phishing attack *1
- Users are 3x more likely to fall for phishing on mobile *2 than desktop

Apps where mobile phishing attacks originate
| Messaging | (17.3%) | +170% increase on 2017 |
| Social media | (16.4%) | +102% increase on 2017 |
| Dating | (6.2%) | |
| Gaming | (11.3%) | |
| (15.4%) | ||
| Sports | (6.2%) | |
| News and weather | (3%) | |
| Productivity | (10.2%) | |
| Travel | (2.1%) | |
| Ecommerce | (5.3%) | |
| Music | (1.3%) | |
| Food and drink | (2.2%) | |
| Finance | (1%) | |
| Health and fitness | (2.1%) |
Top 5 Apps for Mobile Messaging Phishing
- Messenger (inbuilt iOS/Android)
- Facebook Messenger
- LINE
- Viber
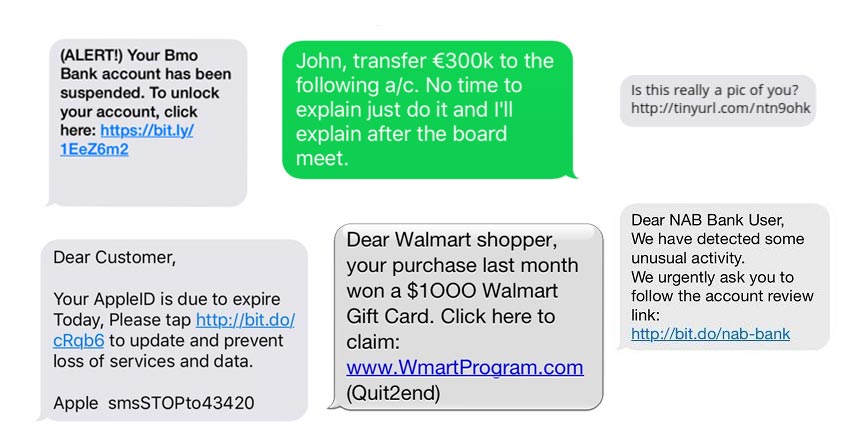
SMS + Phishing = SMishing
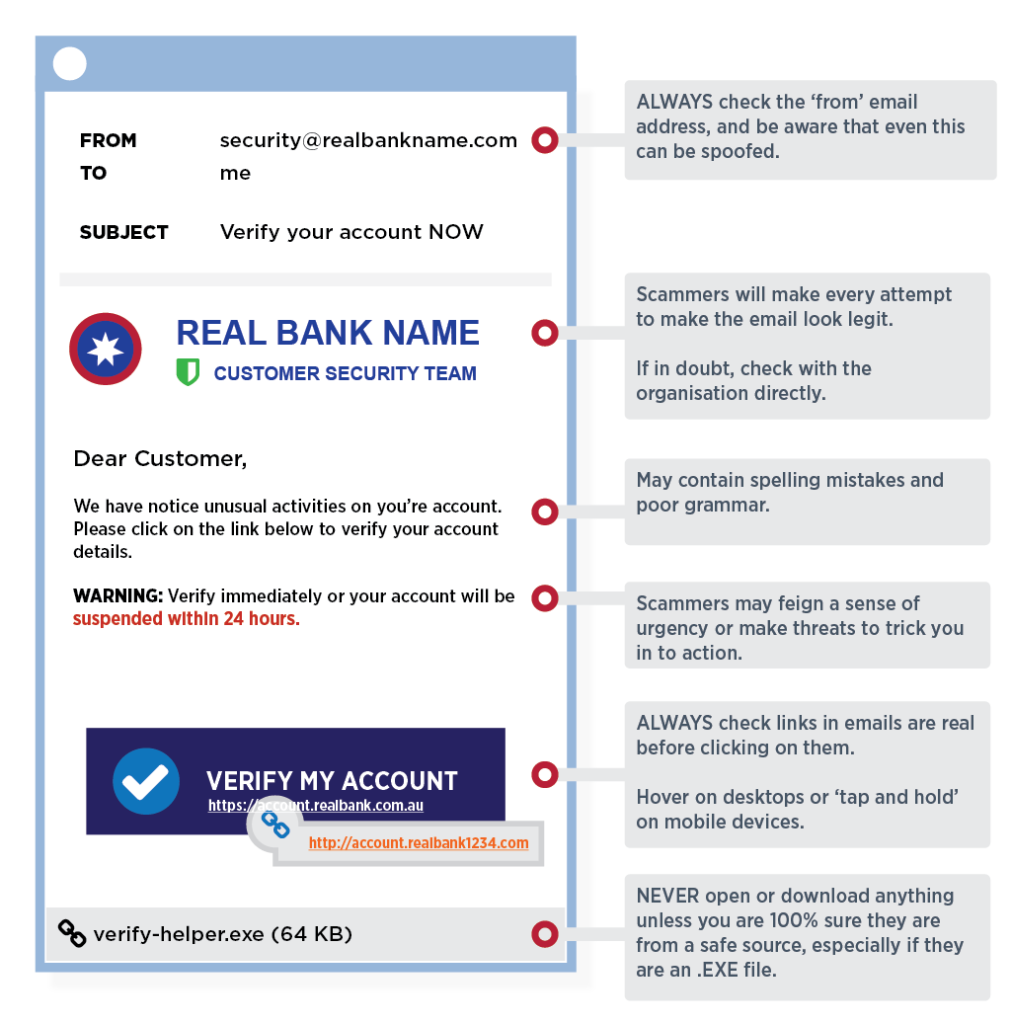
Here’s some screenshots of smishing:
Top 10 brands targeted by phishing attacks
1. Facebook
2. Apple
3. Google
4. Amazon
5. Paypal
6. Government sites
7. Microsoft
8. Fox News
9. Dropbox
10. WhatsApp
It’s harder to spot a phishing website on a mobile device than on a computer
Here’s the difficulty most mobile users experience per device:
BlackBerry:
The “From” field does not include the sender’s address. Instead, it includes the name of the sender, such as “Company ABC”. Although it’s possible to spoof an email address, some users won’t click the link if the entire address is visible and appears “phishy.”
In HTML email, when the user clicks the link, the BlackBerry device shows the following message”Continue to” with the real URL appended. This is a security flaw because BlackBerry’s screen size is limited. It will show a less characters and can appear to be a legitimate website such as “www.wellsfarg…” when the real like is actually, “www.wellsfargo,com.jgydykiyutututkiuhq..”
Even when the BlackBerry starts to load the fraudulent website, and switches to the browser, the top bar only shows the website name created by the phisher. The real address is not shown. If the phishing website appears to look as good as the real one, there’s no easy way to determine if the website is legitimate.
iPhone:
When a user clicks on a link, iPhone’s don’t ask the user if they want to open the URL, instead they automatically load the page. Similar to the BlackBerry, the iPhone has limitations displaying the length of the address bar. If the URL is well crafted like the example above, it’s hard to determine the legitimacy of the URL.
Android:
Same issue as iPhone.
Recommendations:
Mobile users: Do not click on links in email messages since it’s very difficult to determine who sent the email, and the real URL. If you choose to go to a link, type the company’s URL into your browser yourself instead of clicking on the link. For example, if you receive an email the looks like it really came from Amazon.com and you can’t determine if it’s legitimate, go to your trusted amazon app or type “amazon.com” directly into your browser instead.

Sources:
1. http://www.verizonenterprise.com/verizon-insights-lab/dbir/
2. https://securityintelligence.com/mobile-users-3-times-more-vulnerable-to-phishing-attacks/
3. https://globenewswire.com/news-release/2018/05/08/1498518/0/en/Wandera-Report-Finds-Phishing-Attacks-are-Moving-to-Mobile-Messaging-and-Social-Apps-at-an-Alarming-Rate.html
4. http://hyphenet.com/smishing-scam-awareness/
Mobile Phishing screenshot example image: https://www.scamwatch.gov.au/types-of-scams/attempts-to-gain-your-personal-information/phishing